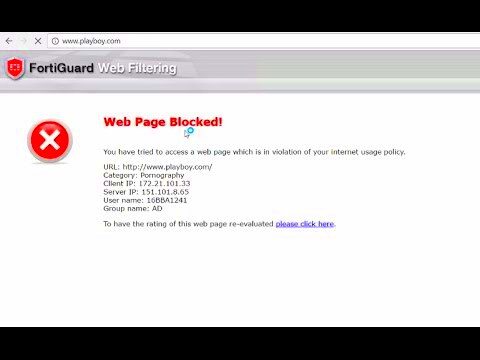
Fortiguard's Intrusion Prevention System (IPS) is designed to protect networks by detecting and blocking potential security threats. It works by analyzing incoming and outgoing data, ensuring no malicious activities slip through. This system is widely used in corporate environments where data security is crucial.
The IPS constantly monitors traffic for known vulnerabilities and suspicious behavior, stopping threats before they can cause harm. While it provides robust protection, it can sometimes block legitimate downloads or access, making it challenging for users who need to download certain content or images.
Why Fortiguard Blocks Certain Download Requests
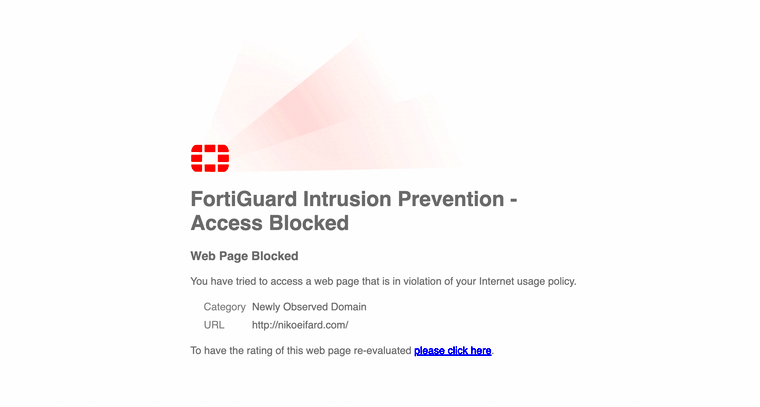
Fortiguard is programmed to block download requests that may appear suspicious or harmful to the network. Its focus is on protecting users from malicious software, ransomware, or unauthorized access to sensitive data. This can include blocking image and file download requests from unfamiliar or flagged sources.
Some common reasons for blocked downloads include:
- Suspicious file types: Certain file extensions or formats might be flagged as potentially harmful.
- Unverified sources: If a website or server isn’t trusted, Fortiguard may block access to its content.
- Known vulnerabilities: Fortiguard regularly updates its threat database, blocking sites with reported vulnerabilities or malicious activity.
While these blocks are put in place to protect users, they can sometimes be an inconvenience when downloading legitimate content like images or media files.
Also Read This: Making a folder in Behance
Common Methods to Bypass Fortiguard Blocks
For users needing to download blocked files or images, there are several methods to bypass Fortiguard’s restrictions. It's essential to remember that these methods should be used responsibly, ensuring you don’t compromise network security. Here are some of the most common techniques:
- Using a VPN: A VPN masks your online activity, helping you bypass Fortiguard’s filters by routing your connection through a different server.
- Proxy Servers: Similar to a VPN, proxy servers allow you to access blocked content by acting as an intermediary between your device and the restricted website.
- Changing DNS Settings: By switching to an alternate DNS provider, you might bypass Fortiguard's filtering mechanisms.
- Downloading from an Alternate Source: Sometimes, finding a different, trusted source for the same file or image can resolve the issue without any technical workarounds.
Each of these methods comes with its risks and benefits. It's crucial to evaluate which approach works best for your situation, keeping in mind security and privacy concerns.
Also Read This: Understanding LinkedIn Endorsements and Their Impact
How to Use a Fortiguard Image and Photo Downloader Tool
Using a Fortiguard image and photo downloader tool can make the process of accessing blocked content easier, especially when you need specific images for work or personal projects. While these tools are designed to help bypass restrictions, it’s important to use them properly to ensure you don’t compromise security or break any rules.
Here’s a step-by-step guide on how to use such a downloader:
- Select a reliable downloader: Make sure to choose a trustworthy tool that’s been reviewed for safety. The ImgPanda Fortiguard Downloader, for instance, is a popular option.
- Install or access the tool: Some downloaders work as browser extensions, while others are standalone software. Follow the instructions provided on the tool’s website to install it on your system.
- Enter the URL of the blocked image: Once the tool is ready, you will need to paste the URL of the blocked image or file into the downloader.
- Start the download: Click the "Download" button, and the tool will bypass Fortiguard’s filters to retrieve the image or photo for you.
- Save the file: Once downloaded, choose a location on your device to save the image, making it accessible for offline use.
Remember to always scan downloaded files for potential threats before opening them, as bypassing security filters can sometimes expose your system to risks.
Also Read This: Canva Transparent Image Creation
Best Practices for Safe Bypassing
While bypassing Fortiguard’s restrictions may seem straightforward, it's important to follow best practices to ensure your safety and maintain the security of your network. Here are some recommendations:
- Use trusted tools: Stick to verified downloader tools that have positive reviews and a good reputation.
- Enable antivirus protection: Always have an updated antivirus program running to detect any potential threats from downloaded files.
- Download from reliable sources: Avoid unknown or suspicious websites, as they can host harmful content.
- Regularly update your system: Ensure that your operating system and all software are up-to-date to protect against known vulnerabilities.
- Limit bypassing to necessary cases: Only bypass Fortiguard blocks when absolutely necessary, and ensure that you’re not violating any network policies or guidelines.
Following these practices will help you stay safe while using Fortiguard image downloader tools, ensuring that you don't expose yourself or your network to avoidable risks.
Also Read This: 3 Ways to Cite a Photograph in APA Format wikiHow
Legal and Ethical Considerations
Bypassing Fortiguard blocks might seem like a harmless way to access restricted content, but there are legal and ethical aspects to consider. Some organizations and networks put these filters in place for legitimate reasons, and circumventing them without permission can lead to consequences.
Here are some legal and ethical factors to keep in mind:
- Company policies: If you’re on a work or school network, bypassing security filters without permission can violate policies, leading to disciplinary action.
- Intellectual property rights: Make sure the content you are downloading is not protected by copyright laws, especially if you plan to use it for commercial purposes.
- Privacy concerns: Downloading blocked content can sometimes expose sensitive information or compromise the security of your network.
It’s always a good idea to seek permission from your network administrator if you need to bypass restrictions for a legitimate reason. This ensures you’re staying within legal boundaries and respecting the rules set by your organization.
Also Read This: How to Successfully Submit Airshow Photos to iStock
FAQs on Bypassing Fortiguard Blocks
When it comes to bypassing Fortiguard blocks, users often have several questions. Below are some common questions and answers to help clarify the process and address any concerns.
Is bypassing Fortiguard legal?
It depends on the context. If you are bypassing restrictions on a network where you have permission, such as your own personal network, it’s usually fine. However, if you’re doing so on a corporate or educational network without permission, you could be violating policies or even laws.
Can bypassing Fortiguard expose my system to threats?
Yes, bypassing security systems can increase the risk of downloading malicious files. It’s important to have up-to-date antivirus software and to be cautious about the content you download.
What is the safest method for bypassing Fortiguard?
Using a VPN is often considered one of the safer methods because it encrypts your data. However, each method has its own risks, and the safest choice will depend on your specific situation and needs.
Will using a Fortiguard downloader tool slow down my internet?
In most cases, using a downloader tool shouldn’t significantly impact your internet speed. However, if you are using a VPN or proxy, you might experience a slight reduction in speed due to encryption and rerouting of data.
Do I need technical knowledge to bypass Fortiguard blocks?
Basic knowledge of VPNs, proxies, or downloader tools is helpful, but most tools available today are user-friendly and provide clear instructions for beginners.
Final Thoughts on Bypassing Fortiguard’s Intrusion Prevention
Bypassing Fortiguard’s blocks can be useful in certain situations, but it’s important to weigh the legal, ethical, and security implications. Always ensure you’re using safe methods and have a legitimate reason for bypassing the system to avoid potential risks.